Cloudflare Origin Certificate
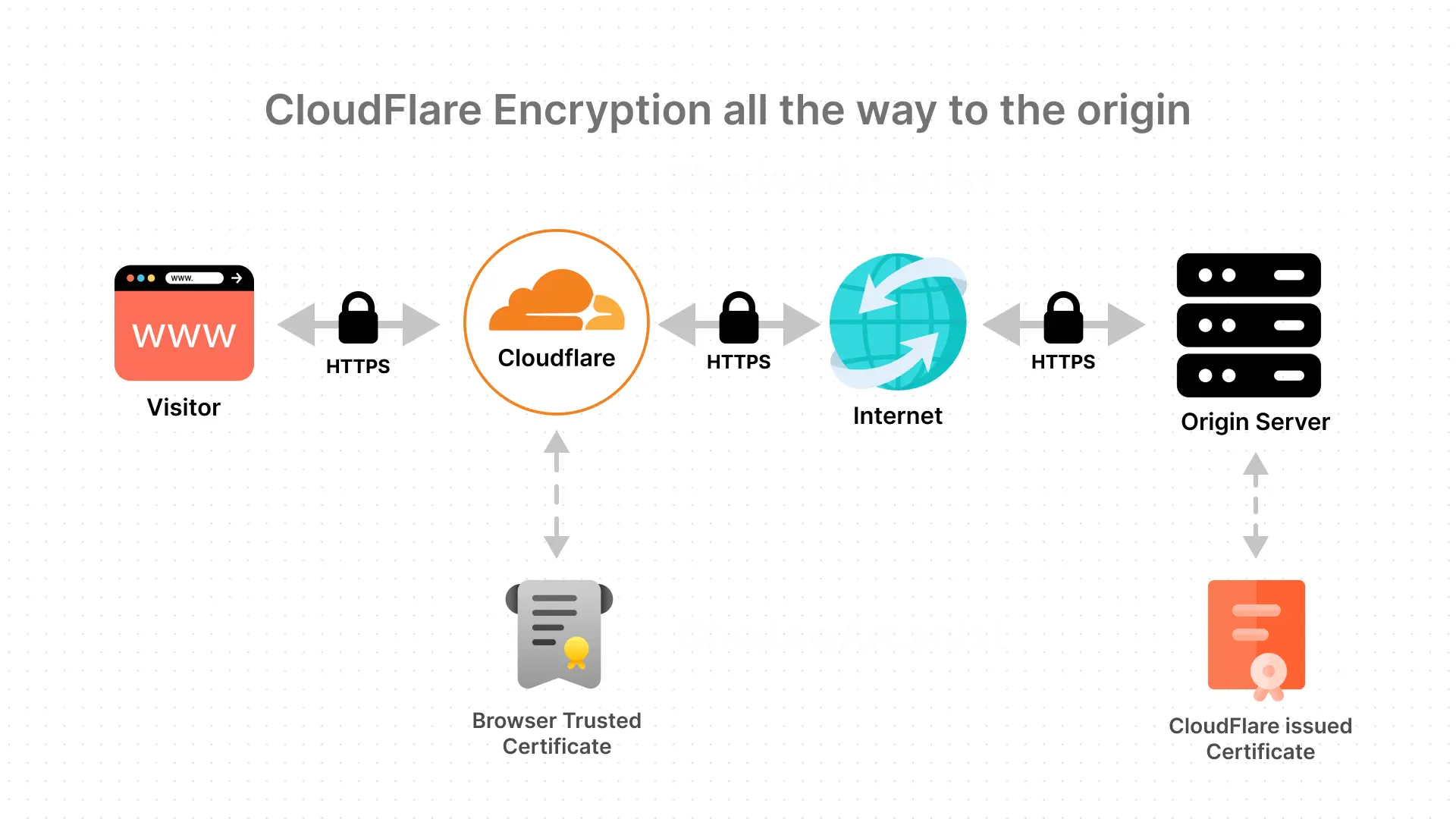
The Cloudflare Origin Certificate ensures secure communication between your server and Cloudflare when using Cloudflare’s Proxy, CDN, and security features.
It encrypts the data exchanged between your server and Cloudflare, keeping it safe.
Why Use Cloudflare Origin Certificate with Coolify?
- No need for HTTP or DNS challenges to create certificates.
- Keep port 80 closed — everything happens securely over TLS.
- Longer certificate validity (15 years) — once set up, you don’t need to worry about renewing every few months.
When to Avoid Using Cloudflare Origin Certificate
- If you need a free certificate for subdomains with multiple levels (e.g., app.sub.domain.com).
- The certificate is only trusted by Cloudflare, meaning if Cloudflare is down, nobody can access your apps and websites (via your domain).
Example Data
The following data is used as an example in this guide. Please replace it with your actual data when following the steps:
- IPv4 Address of Origin Server: 203.0.113.1
- Domain Name: shadowarcanist.com
- Username: shadowarcanist
1. Create the Origin Certificate
To create your Cloudflare Origin Certificate, follow these steps:
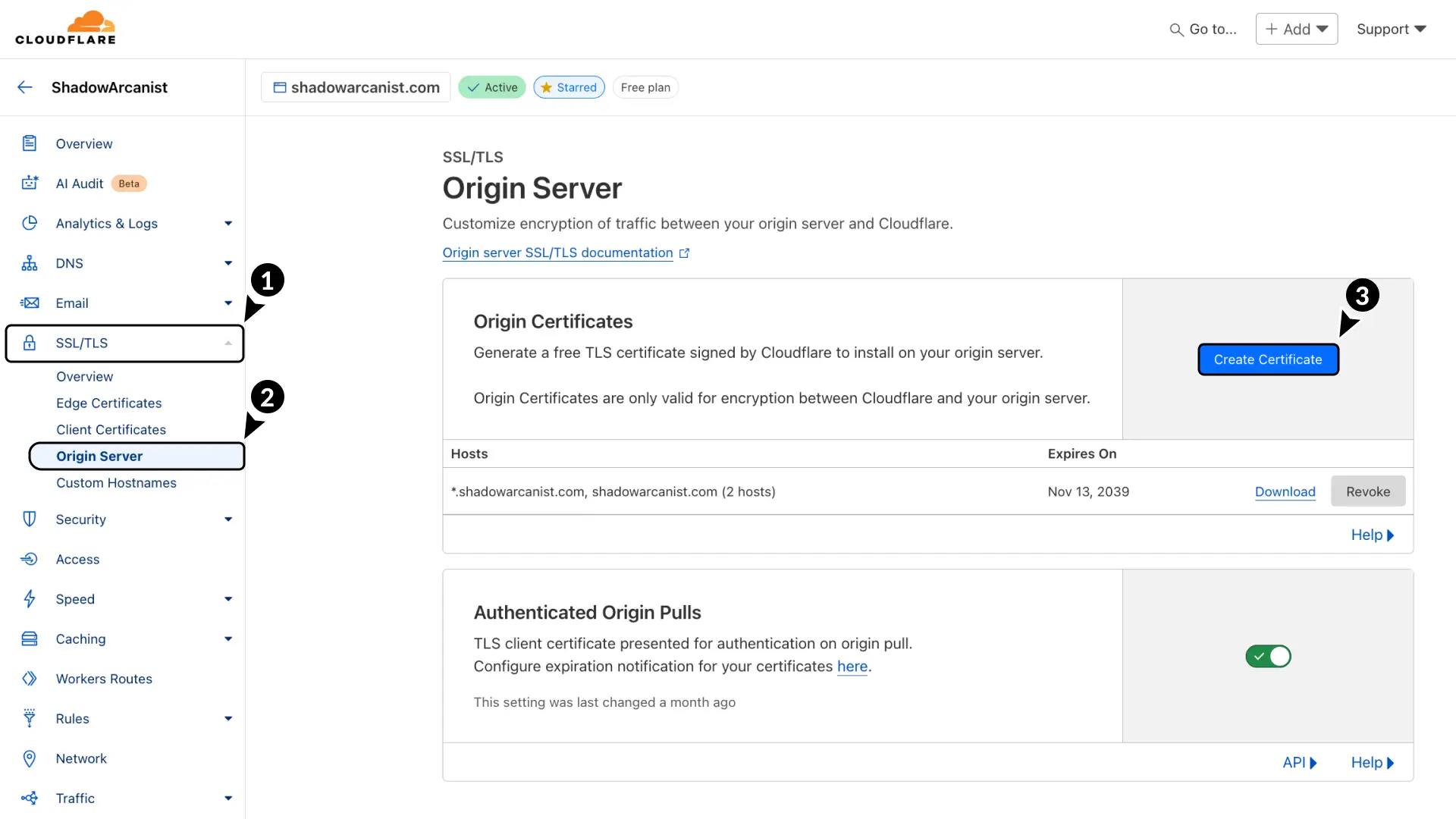
- In your Cloudflare dashboard, go to SSL/TLS.
- Select Origin Server.
- Click the Create Certificate button.
You’ll be asked to choose a private key type, hostnames, and certificate validity.
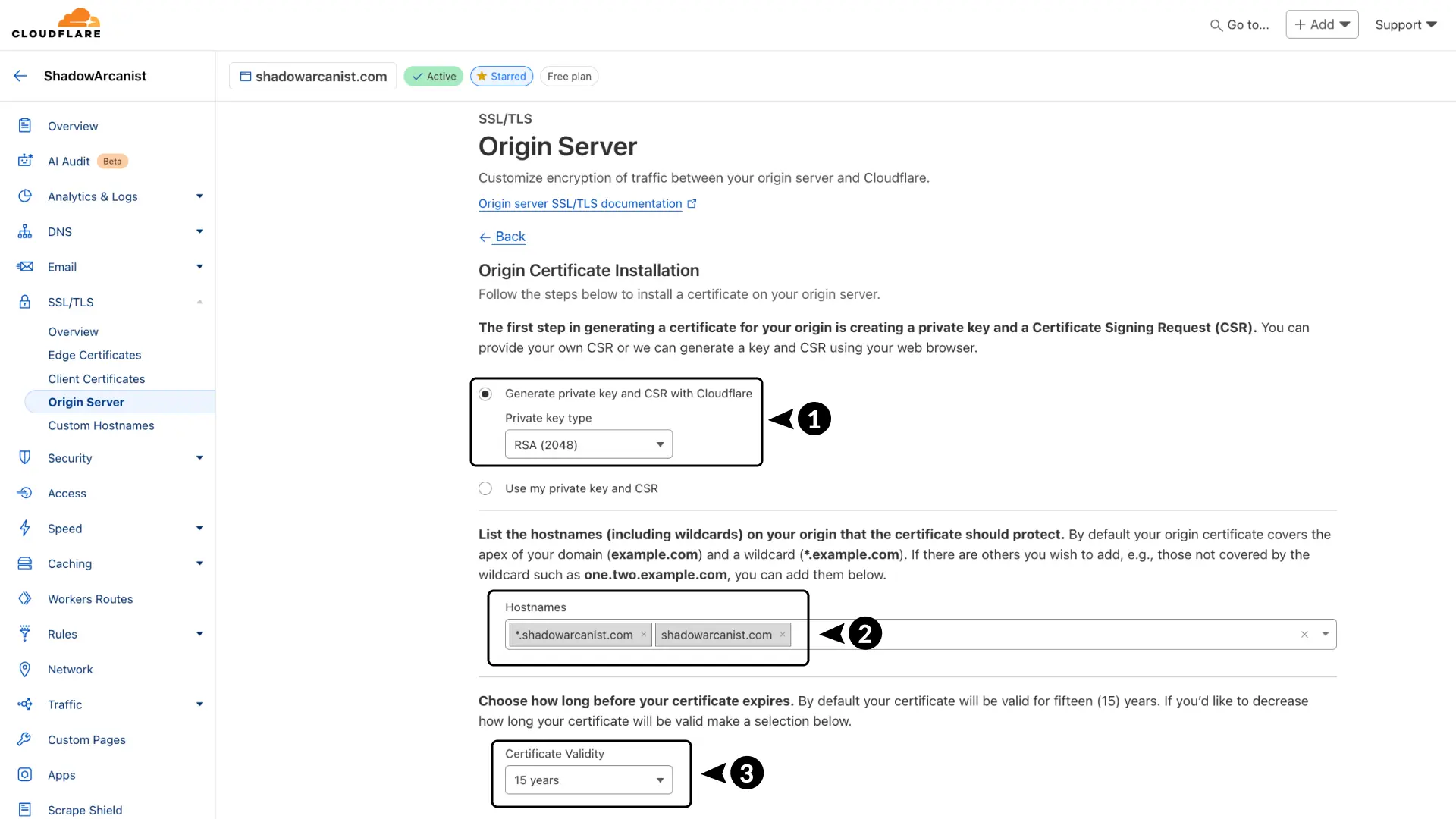
- Choose RSA (2048) for the key type.
- Add the hostnames you want the certificate to cover.
HEADS UP!
shadowarcanist.comwill cover only the main domain.*.shadowarcanist.comwill cover all subdomains.
On Cloudflare’s free plan, wildcard certificates cover just one level of subdomains
For example, it works for coolify.shadowarcanist.com but not www.coolify.shadowarcanist.com.
To cover multiple levels, you'll need to purchase the Advanced Certificate Manager
- Set the certificate validity to 15 years.
Your certificate will now be generated.
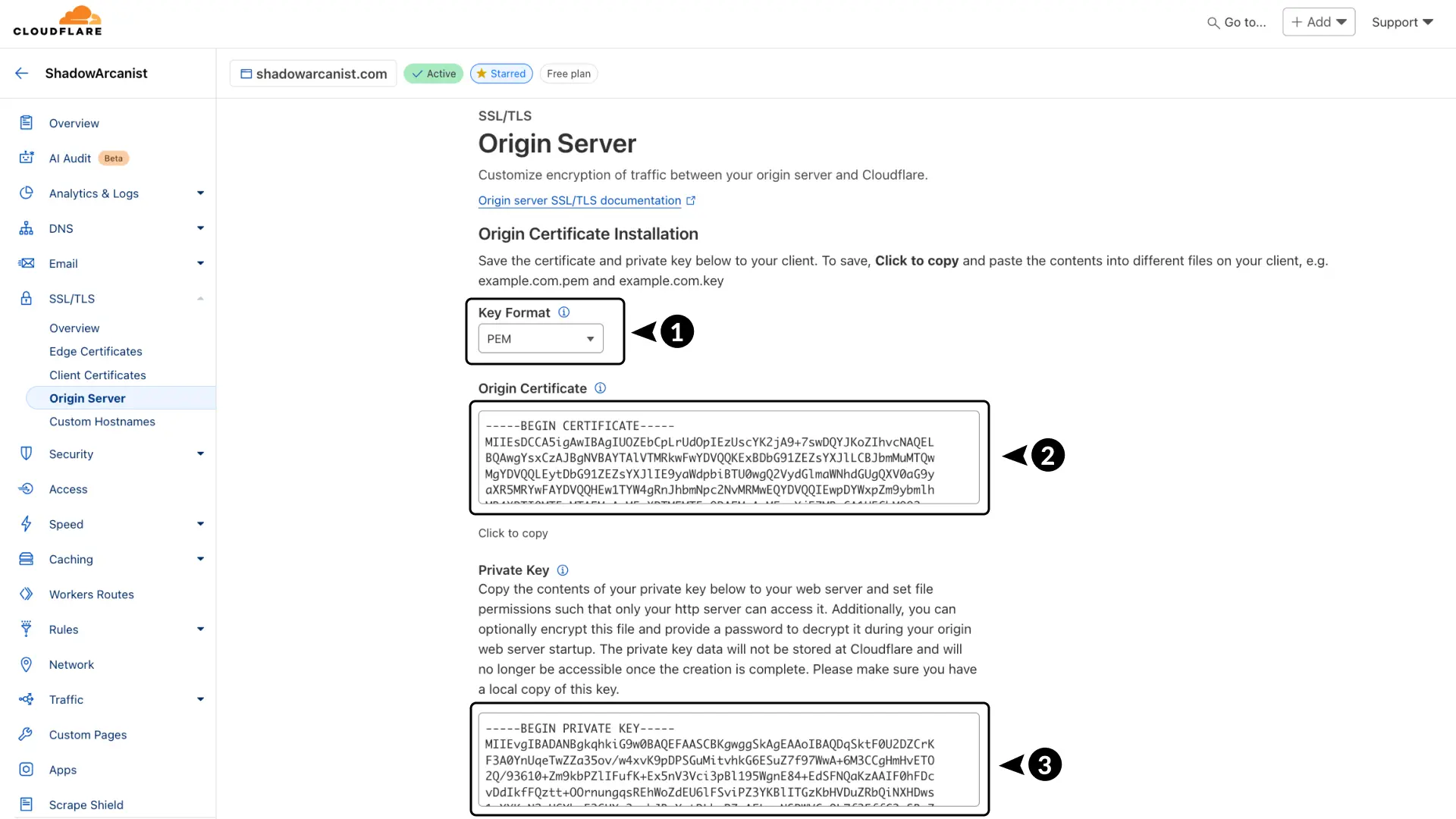
- Choose PEM as the key format.
- Copy your Certificate.
- Copy your Private Key.
Next, you'll add these to your server running Coolify and configure Coolify to use this certificate.
2. Add Certificate to Your Server
SSH into your server or use Coolify's terminal feature. For this guide, I’m using SSH:
ssh [email protected]Once logged in, navigate to the Coolify proxy directory:
$ cd /data/coolify/proxyCheck if you have a certs folder:
$ ls
> acme.json docker-compose.yml dynamicIf there’s no certs folder, create it:
$ mkdir certsVerify it was created:
$ ls
> acme.json certs docker-compose.yml dynamicNow, navigate into the certs directory:
$ cd certsCreate two new files for the certificate and private key:
$ touch shadowarcanist.cert shadowarcanist.keyVerify the files were created:
$ ls
> shadowarcanist.cert shadowarcanist.keyOpen the shadowarcanist.cert file and paste the certificate from the Cloudflare dashboard:
$ nano shadowarcanist.certSave and exit after pasting the certificate.
Do the same for the shadowarcanist.key file and paste the private key:
$ nano shadowarcanist.keySave and exit.
Now the origin certificate is installed on your server.
3. Set Up DNS Records and TLS Encryption
To make the origin certificate work, configure your DNS records, enable TLS, and set up HTTP to HTTPS redirects in Cloudflare:
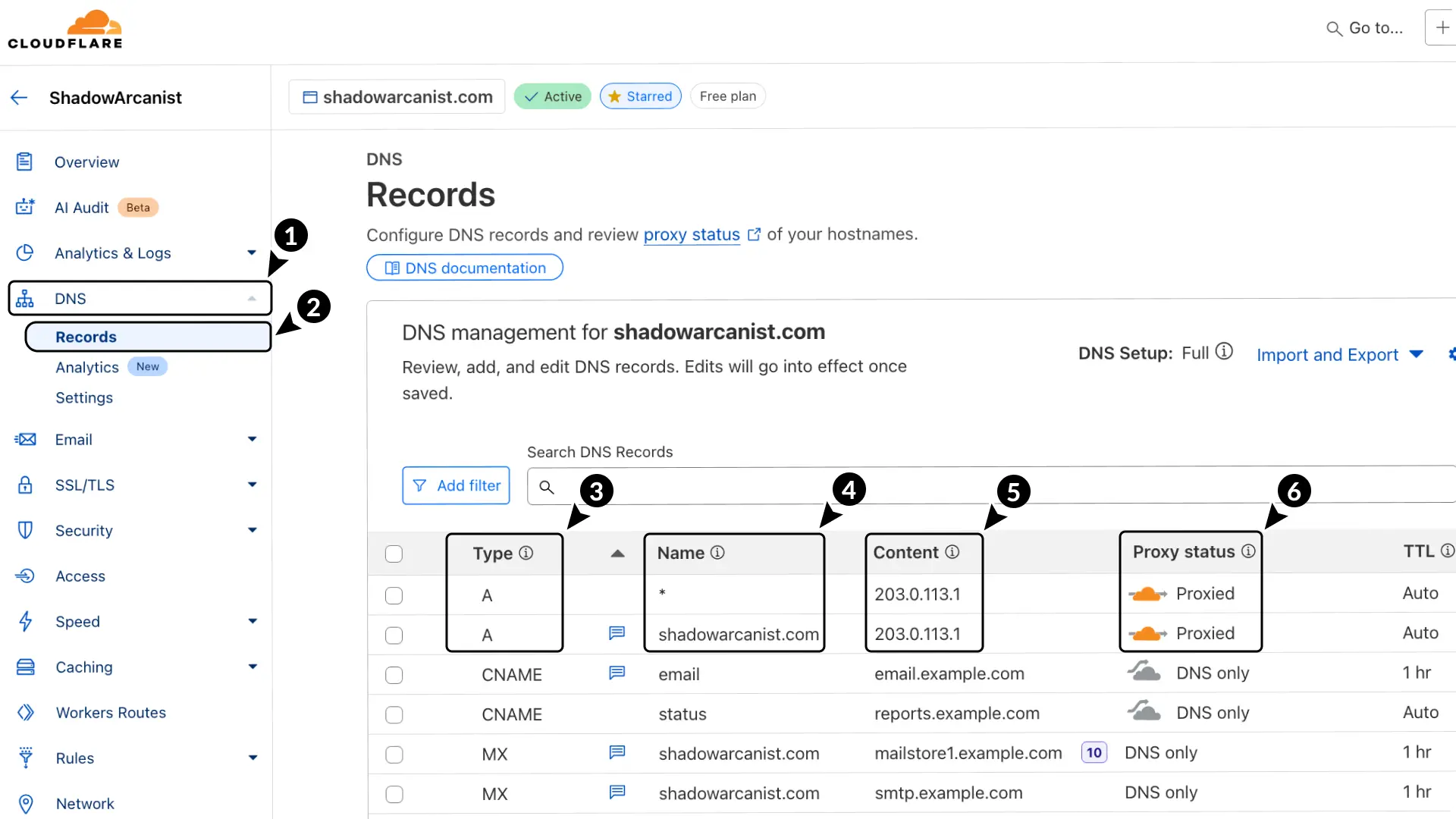
- In Cloudflare, go to DNS.
- Select Records.
- Add 2 A records:
- Enter name as
shadowarcanist.comand* - Use the IP address of your server as the content for both records.
- Set the proxy status to Proxied for better security.
Next, set up TLS encryption:
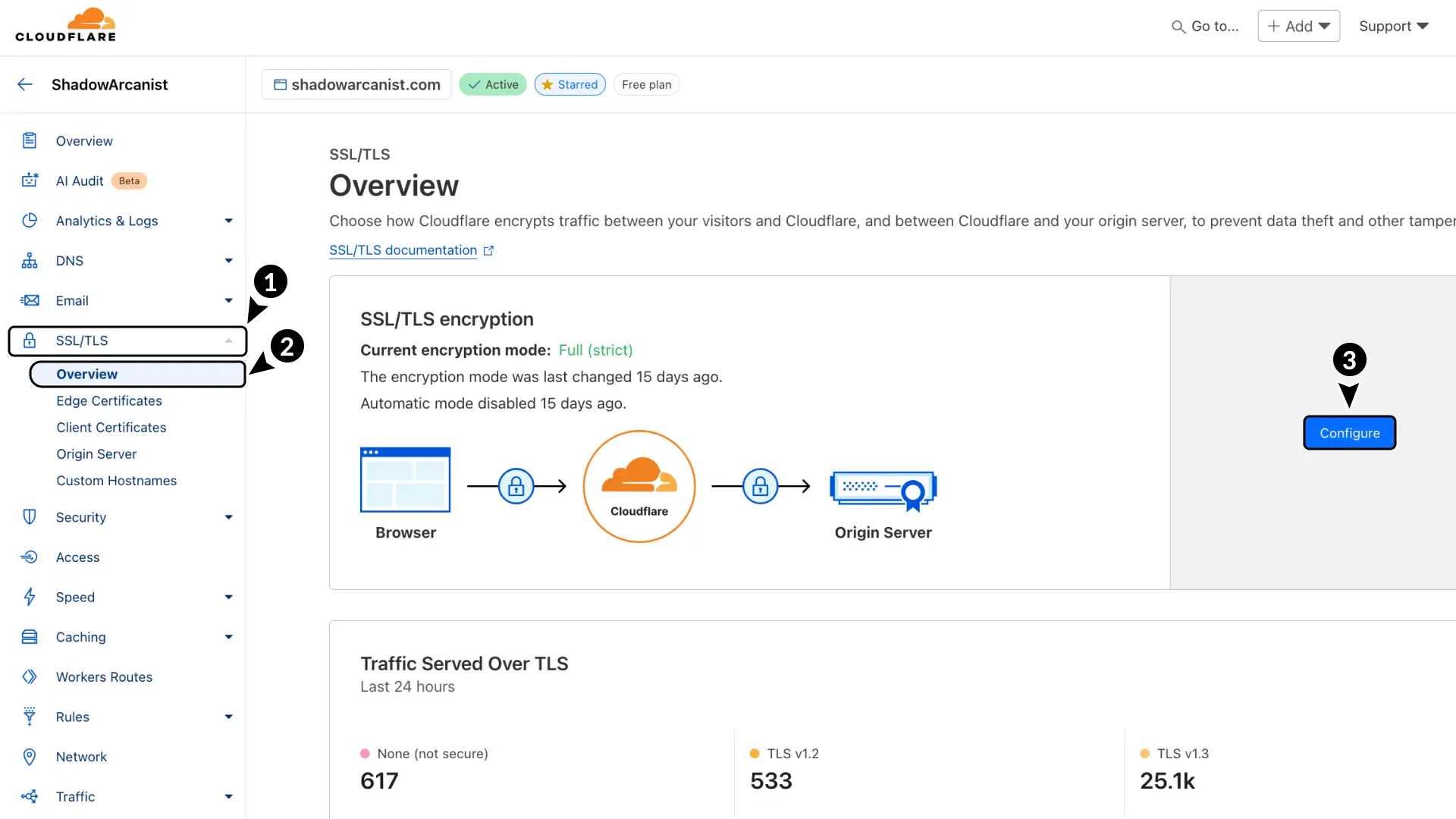
- Go to SSL/TLS in Cloudflare.
- Select Overview.
- Click Configure button
Choose Full (Strict) as the encryption mode.
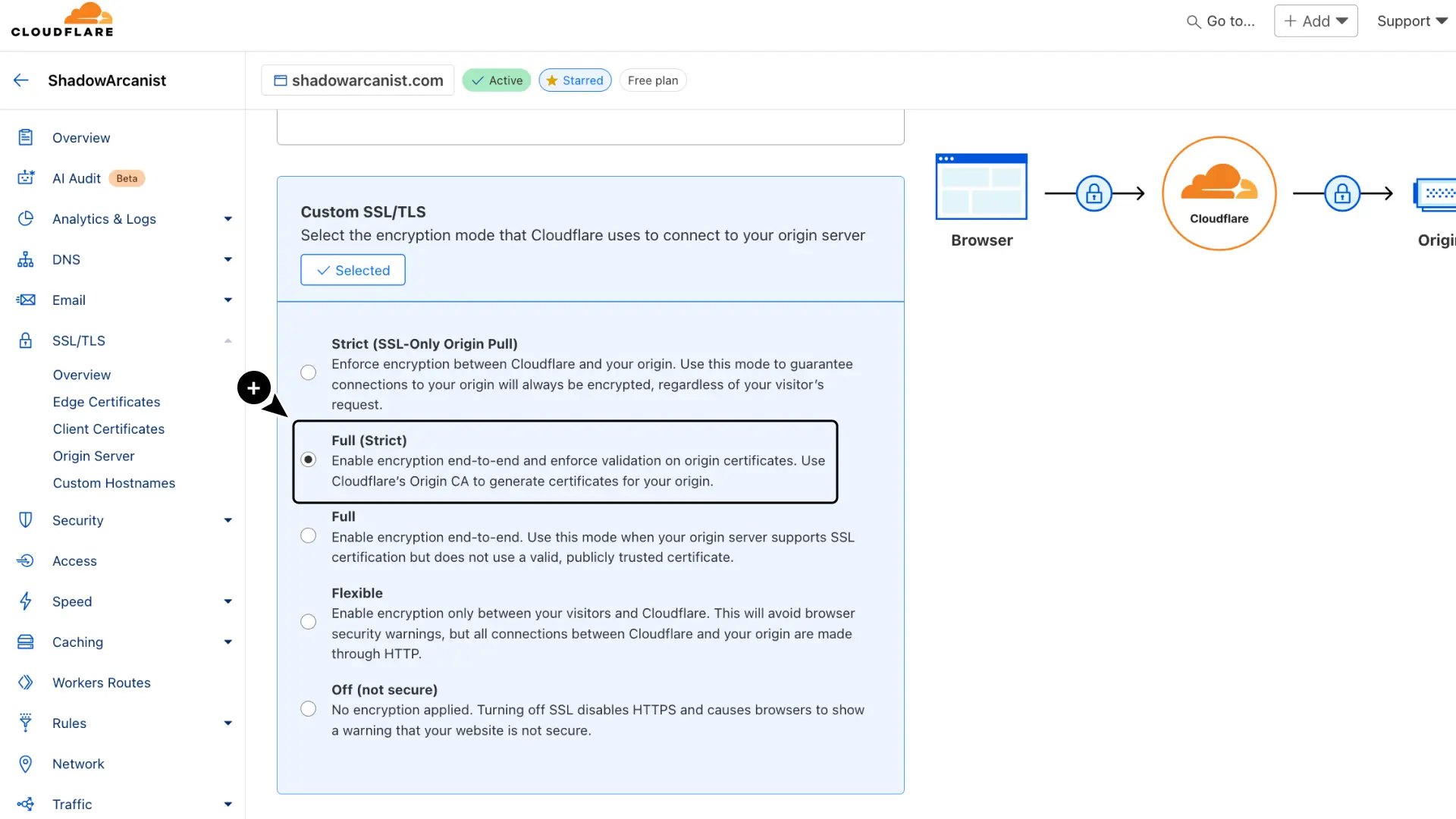
Finally, enable HTTP to HTTPS redirects:
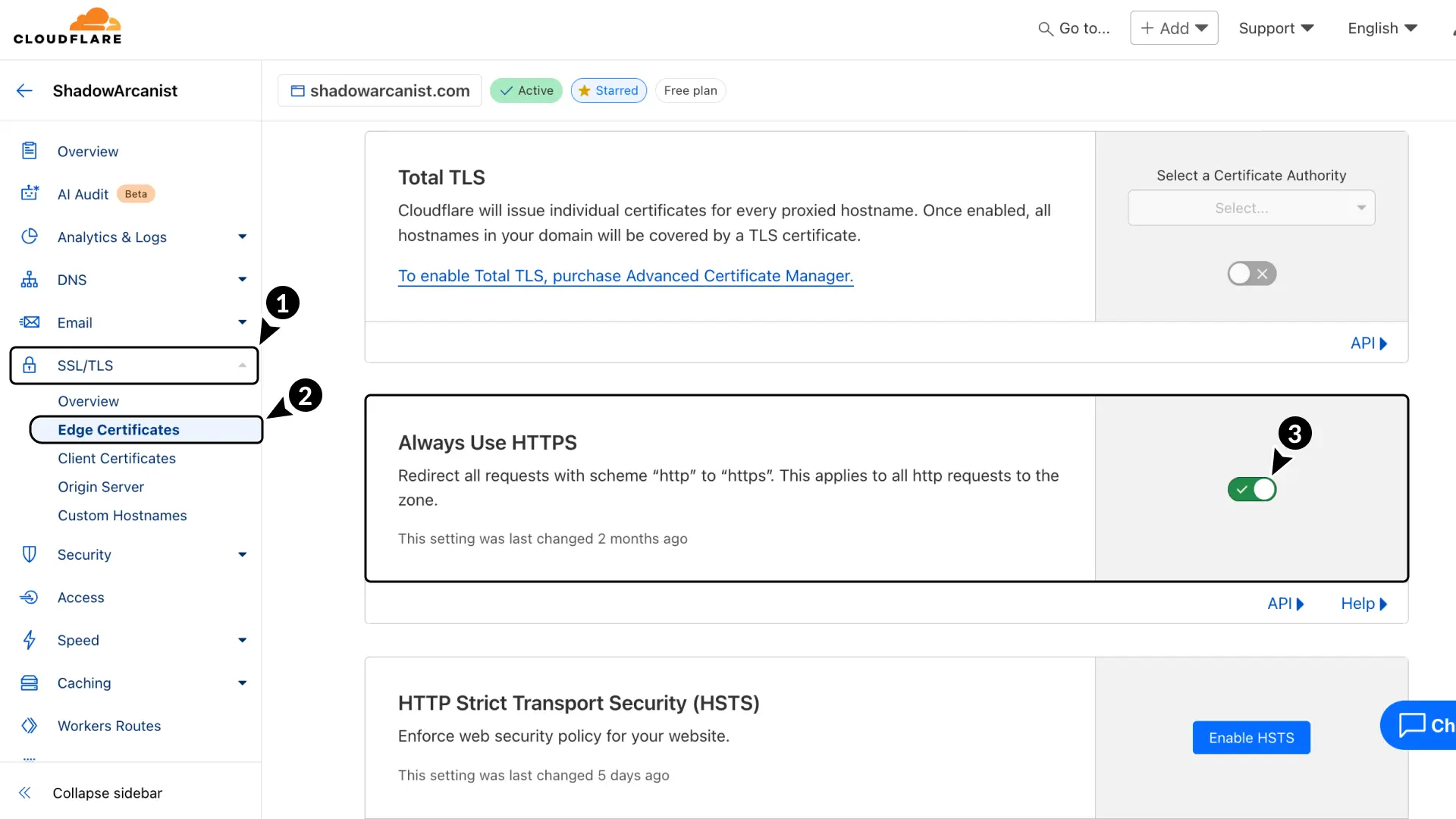
- In Cloudflare, go to SSL/TLS
- Select Edge Certificates.
- Enable Always Use HTTPS.
4. Configure Coolify to Use the Origin Certificate
Now, in your Coolify dashboard:
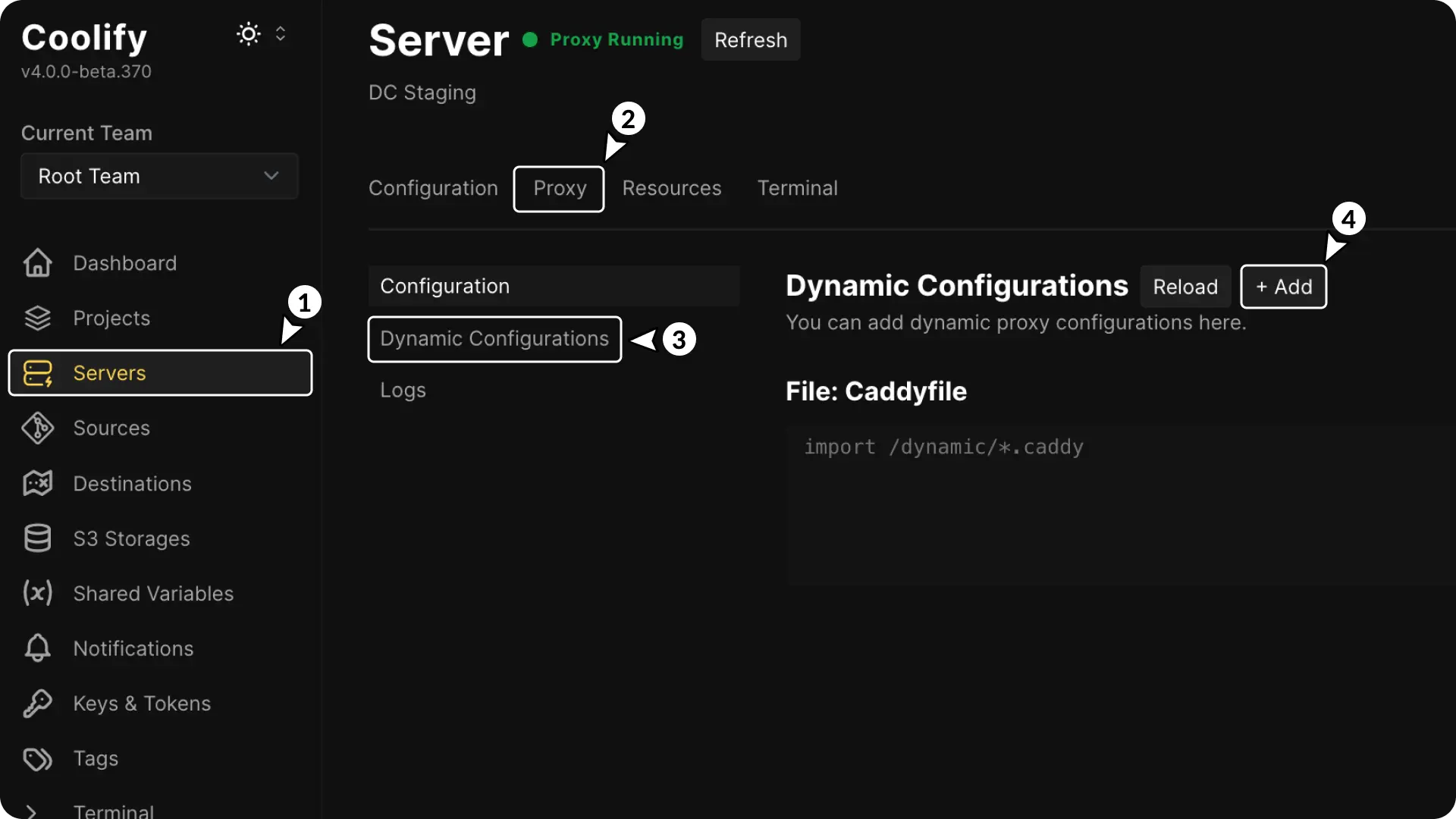
- Go to the Server section in the sidebar.
- Select Proxy.
- Open the Dynamic Configuration page
- Click Add button
You will now be prompted to enter the Dynamic Configuration.
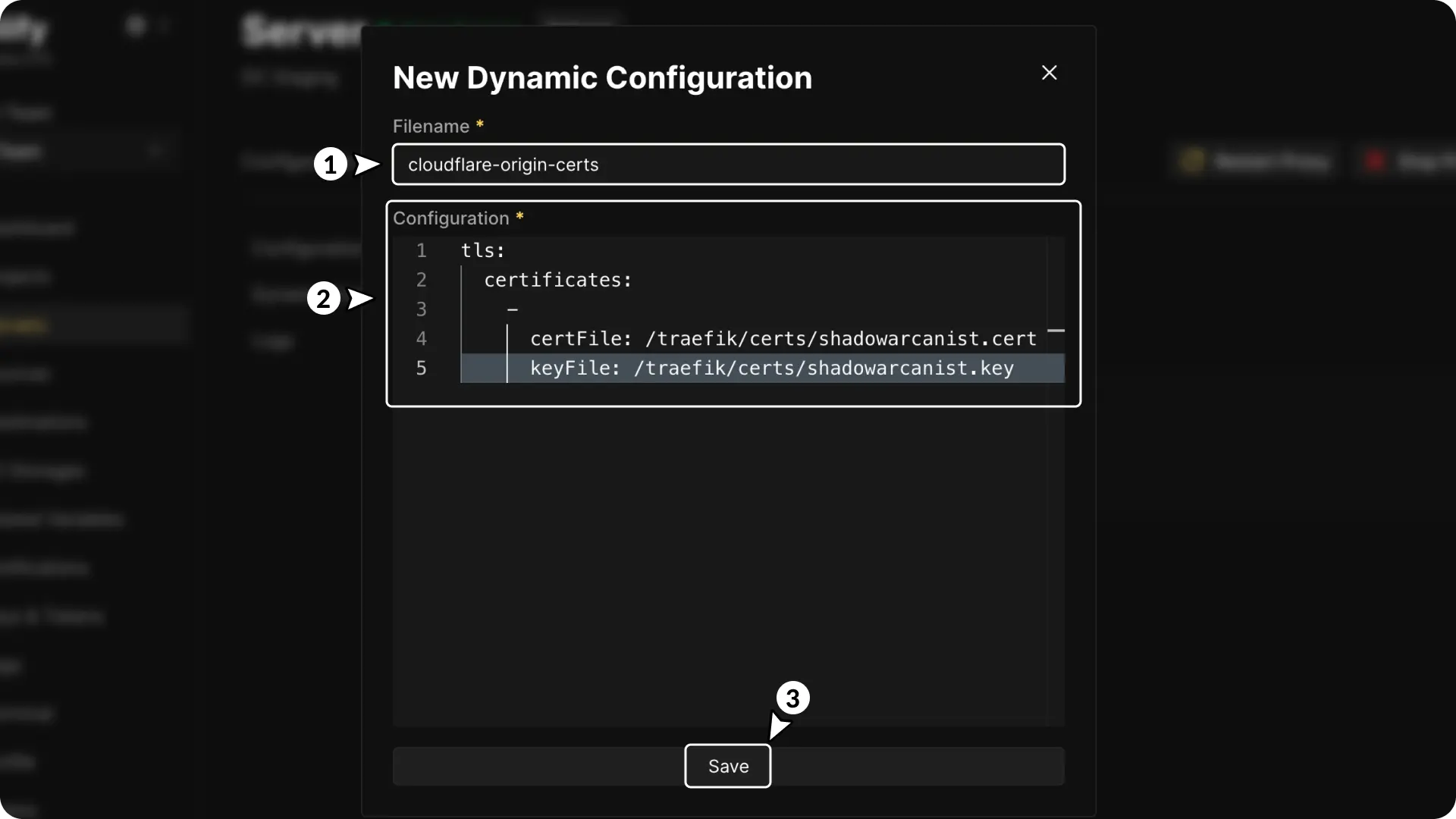
- Choose a name for your configuration.
- Enter the following details in the configuration field:
tls:
certificates:
-
certFile: /traefik/certs/shadowarcanist.cert
keyFile: /traefik/certs/shadowarcanist.keyAdding Multiple Certificates (click to view)
tls:
certificates:
-
certFile: /traefik/certs/shadowarcanist.cert
keyFile: /traefik/certs/shadowarcanist.key
-
certFile: /traefik/certs/name2.cert
keyFile: /traefik/certs/name2.key
-
certFile: /traefik/certs/name3.cert
keyFile: /traefik/certs/name3.key- Save the configuration
From now on, Coolify will use the origin certificate for requests matching the hostname.
HEADS UP!
All the steps below are optional. Coolify should already be using the origin certificate. Follow these steps only if you know what you're doing and want to simplify the configuration
5. Optional: Configure Traefik
This step is optional but recommended for cleaning up unnecessary settings while self-hosting.
Since you’re using an Origin Certificate, you no longer need HTTP challenges or port 80 open.
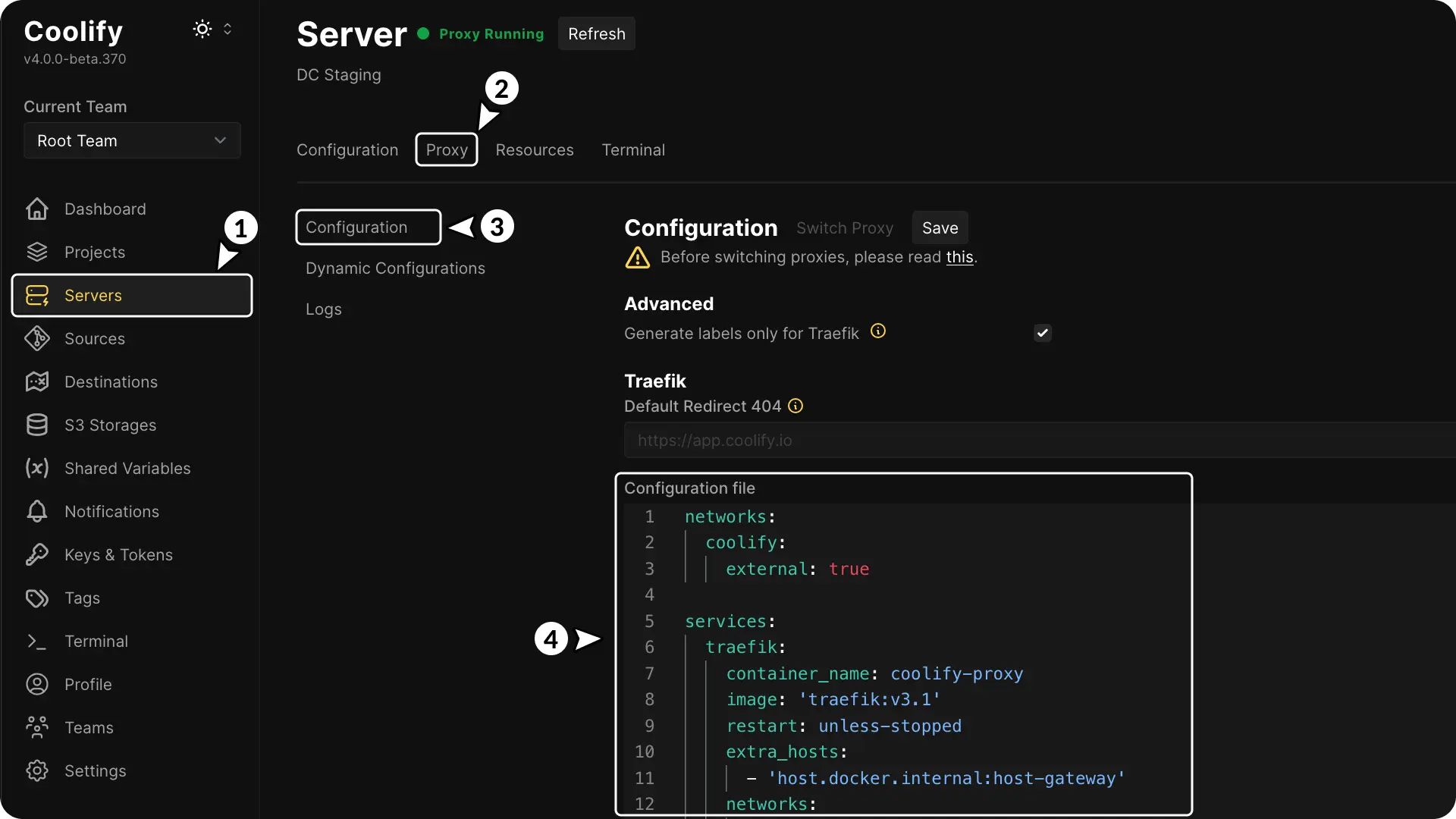
- Go Server in the Coolify dashboard.
- Select Proxy.
- Open Configuration.
- Replace the configuration with this:
# Define external networks
networks:
coolify:
external: true # External network.
services:
# Traefik reverse proxy
traefik:
container_name: coolify-proxy # Container name.
image: 'traefik:v3.1' # Traefik image version.
restart: unless-stopped # Auto-restart policy.
extra_hosts:
- 'host.docker.internal:host-gateway' # Host communication.
networks:
- coolify # Network connection.
ports:
- '443:443' # Expose HTTPS port.
healthcheck: # Health check configuration.
test: 'wget -qO- http://localhost:80/ping || exit 1' # Ping endpoint for health check.
interval: 4s # Health check interval.
timeout: 2s # Health check timeout.
retries: 5 # Retry attempts.
volumes:
- '/var/run/docker.sock:/var/run/docker.sock:ro' # Docker socket access.
- '/data/coolify/proxy:/traefik' # Traefik config volume.
command:
# Traefik configuration options
- '--ping=true' # Enable ping for health check.
- '--ping.entrypoint=http' # Use HTTP entrypoint for ping.
- '--entrypoints.http.address=:80' # HTTP entry point for health checks.
- '--entrypoints.https.address=:443' # HTTPS entry point.
- '--entrypoints.http.http.encodequerysemicolons=true' # Enable query semicolon encoding.
- '--entryPoints.http.http2.maxConcurrentStreams=50' # HTTP/2 max streams.
- '--entrypoints.https.http.encodequerysemicolons=true' # Enable HTTPS query encoding.
- '--entryPoints.https.http2.maxConcurrentStreams=50' # HTTPS/2 max streams.
- '--entrypoints.https.http3' # Enable HTTP/3.
- '--providers.docker.exposedbydefault=false' # Disable default exposure.
- '--providers.file.directory=/traefik/dynamic/' # Dynamic config directory.
- '--certificatesresolvers.letsencrypt.acme.httpchallenge=false' # Disable HTTP challenge for Let's Encrypt.
- '--providers.file.watch=true' # Enable config file watching.
- '--providers.docker=true' # Enable Docker provider.
labels:
- coolify.managed=true # Managed by Coolify.
- coolify.proxy=true # Proxy service.Note
The comments in this configuration explain each line. You can remove the comments when copying it into your configuration.
Next, you'll need to remove a few labels from your Dockerfile-based deployments. Below is an example of how I set this up for my website.
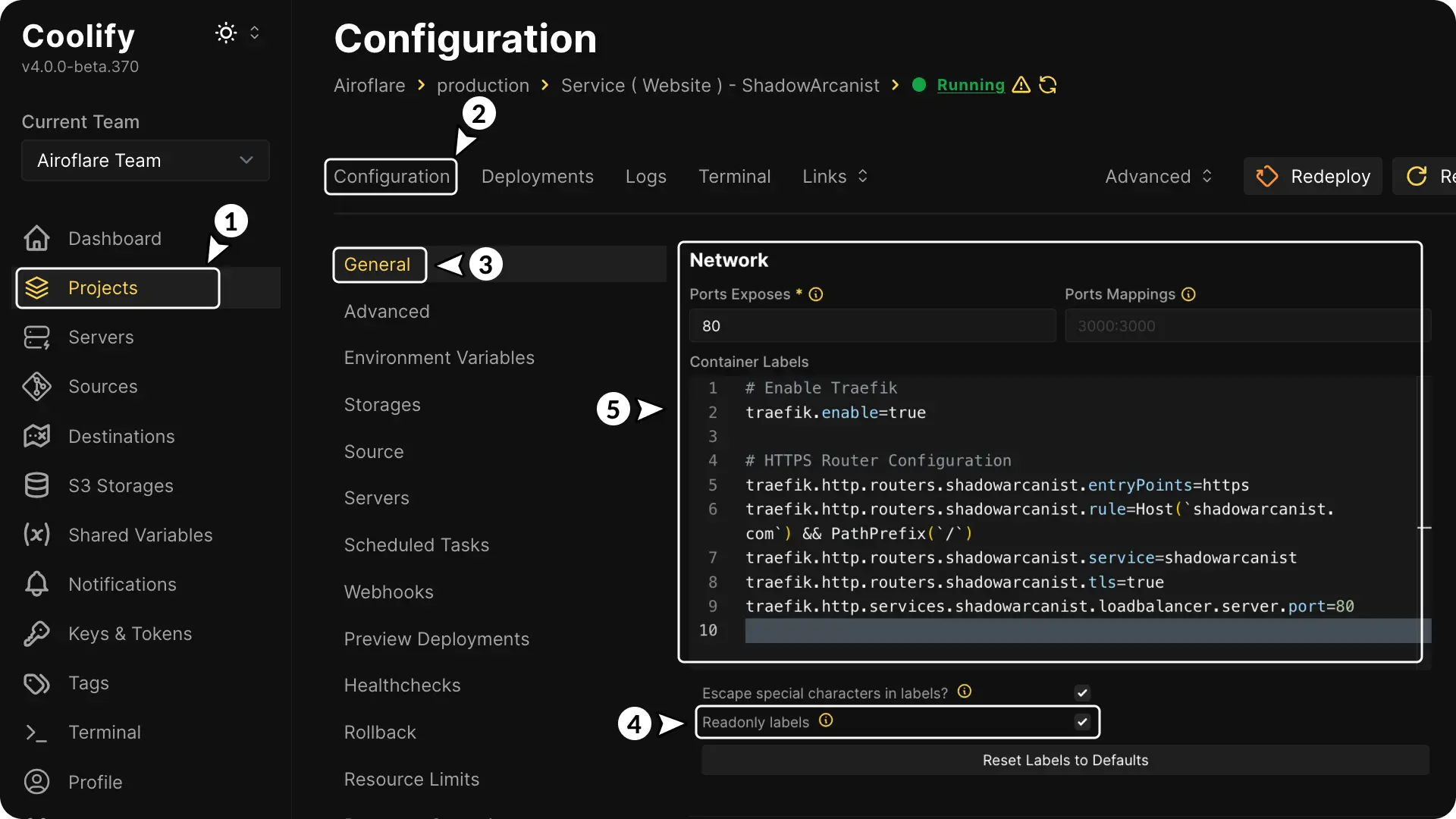
- Go to Projects and select your project.
- Open Configuration
- Go to General
- Check Readonly labels option
- Replace the labels with the following:
# Enable Traefik for this configuration
traefik.enable=true
# Define the entry point for the router (HTTPS)
traefik.http.routers.shadowarcanist.entryPoints=https
# Set the routing rule for this router to match the domain "shadowarcanist.com" and any path starting with "/"
traefik.http.routers.shadowarcanist.rule=Host(`shadowarcanist.com`) && PathPrefix(`/`)
# Assign the service 'shadowarcanist' to this router
traefik.http.routers.shadowarcanist.service=shadowarcanist
# Enable TLS (HTTPS) for this router
traefik.http.routers.shadowarcanist.tls=true
# Specify the backend service and its port (port 80)
traefik.http.services.shadowarcanist.loadbalancer.server.port=80Now you’re done! Your server is set up to use the Cloudflare Origin Certificate, and all traffic is secured via TLS.
Note
Keep in mind that the above labels are provided as an example. These may or may not work for your specific use case, so use them as a reference.
Credits
The header image is designed using icons from Flaticon. Links to each icon can be found below: